The recent Equifax Cybersecurity Breach was an eye opener like no other. The personal information of 145 million Americans were taken, including but not limited to social security numbers, addresses, and credit card numbers. This means that some enterprising and unscrupulous individuals have access to confidential data — and were able to accomplish this with relative ease. In light of this, cybersecurity experts have put out a number of helpful tips to help you maintain your safety online.
Use special passwords:
As much as possible, avoid birthdays, chronological number sequences, literary quotes, and popular song lyrics. According to News.USF.edu, hackers have software to guess and crack passwords in seconds. Instead, use phrases or statements known only to you (“The chair is against the wall”), or the first letters of each word in those statements (“tciatw”).
Don’t use the same password more than once:
Utilizing duplicate passwords for multiple accounts make it easier for hackers to enter these accounts.
Change passwords every six months:
Though this seems tedious, switching up your passwords can make a world of difference.
Avoid clicking on links in emails and opening attachments:
Ensure first that the emails are authentic, meaning that they don’t come from trick email addresses (e.g. “lotsamoney.com”). To check if links are safe, just hover your cursor over them. Doing this will show the address. In line with this, steer clear of any ads or apps in these emails.
Be wary of apps:
If you really must download apps, do so from the app store for your operating system. And before you install them, check to see if they won’t be accessing unnecessary information (e.g. a drawing app doesn’t need to see your contacts list).
Use secure networks:
If you can, avoid using public WiFi networks. They may be convenient, but they’re not secure. Connecting to public WiFi leaves you vulnerable and exposed to any hackers keeping an eye on that particular network. (Related: Software security group demonstrates how hackers can use ransomware to harm and potentially kill hospital patients.)
Keep up to date with security measures:
Make use of antivirus software and ensure that it’s up to date, and make it a point to do the same for any security features your browser and operating system may have. This will give you a much-needed extra layer of protection whenever you’re online. In addition, choose multi-factor authorization. It’s an extra bit of work but totally worth it, since a second level of verification can notify you if and when someone is attempting to hack into your account.
Look for the lock:
Specifically, the little green padlock before the website URL in the web address bar. The padlock serves as an indication to let you know that your login and account information is encrypted and won’t fall victim to unauthorized access.
https://nexusnewsfeed.com/article/science-futures/simple-steps-for-preventing-your-online-presence-from-being-hacked/
Mozilla Launches Firefox Quantum, Poses Real Threat to Google Chrome
Mozilla unveiled the new and improved version 57 of Firefox on Tuesday, claiming that the browser is now twice as fast as before. The company also revealed a new user interface (UI) that looks decidedly minimalist.
https://www.mozilla.org/en-US/firefox/new/
3 Cloud Trends to Watch Out for in 2018

Cloud computing has dominated the business world this year, and the trend will only continue into 2018.
https://www.webpronews.com/3-cloud-trends-watch-2018-2017-11/
Web Site Builders
I hand code my emails and web sites so this is by no means an endorsement of any other product. Here is a link to a site that lists a bunch of web site builders with their cost and user rankings.
http://wave.webaim.org/report#/https://digital.com/website-builders/?flag=wave
So I Accidentally Found a Security Vulnerability in Windows 10
About six months ago, in the process of going all Linux, I was selling off an old laptop of mine with an SSD and Windows 10 to a friend. I wanted to securely remove all my data without removing the Windows install since I had lost the OEM key. I recalled seeing Windows 10 having a secure reset feature, described as being designed for easily removing all personal data from your computer before recycling or selling it. That sounded great, and so I pressed the button to start it and the ridiculousness of the last six months of my life began.
http://www.justinkterry.com/2017/09/so-i-accidentally-found-security.html
7 Tips for Presenting Bulleted Lists in Digital Content
Summary: Bullet points help break up large blocks of text, make complex articles and blog posts easier to grasp, and make key information stand out.
https://www.nngroup.com/articles/presenting-bulleted-lists/
3 ways to protect your business from ransomware
In recent months, ransomware has been increasingly garnering headlines here and across the globe. If you’ve been keeping your head down and believe that it won’t happen to you or your business – now is a good time to think again.
Step 1. Prepare a recovery plan: Recover without paying
- What: Plan for the worst-case scenario and expect that it will happen at any level of the organization.
- Why: This will help your organization:
- Limit damage for the worst-case scenario: Restoring all systems from backups is highly disruptive to business, but it’s still more efficient than trying to do recovery using low-quality attacker-provided decryption tools after paying to get the key. Remember: paying is an uncertain path; you have no guarantee that the attackers’ key will work on all your files, that the tools will work effectively, or the attacker—who may be an amateur using a professional’s toolkit—will act in good faith.
- Limit the financial return for attackers: If an organization can restore business operations without paying, the attack has effectively failed and resulted in zero return on investment for the attackers. This makes it less likely they will target your organization again in the future (and deprives them of funding to attack others). Remember: attackers may still attempt to extort your organization through data disclosure or abusing/selling the stolen data, but this gives them less leverage than possessing the only means of accessing your data and systems.
- How: Organizations should ensure they:
- Register risk. Add ransomware to the risk register as a high-likelihood and high-impact scenario. Track mitigation status via your Enterprise Risk Management (ERM) assessment cycle.
- Define and backup critical business assets. Automatically back up critical assets on a regular schedule, including correct backup of critical dependencies, such as Microsoft Active Directory.
- Protect backups. To safeguard against deliberate erasure and encryption, use offline storage, immutable storage, and/or out-of-band steps (multifactor authentication or PIN) before modifying or erasing online backups.
- Test ‘recover from zero’ scenario. Ensure that your business continuity and disaster recovery (BC/DR) can rapidly bring critical business operations online from zero functionality (all systems down). Conduct practice exercises to validate cross-team processes and technical procedures, including out-of-band employee and customer communications (assume all email and chat are down). Important: protect (or print) supporting documents and systems required for recovery, including restoration-procedure documents, configuration management databases (CMDBs), network diagrams, and SolarWinds instances. Attackers regularly destroy these documents.
- Reduce on-premises exposure. Move data to cloud services with automatic backup and self-service rollback.
Step 2. Limit the scope of damage: Protect privileged roles (starting with IT admins)
- What: Ensure you have strong controls (prevent, detect, respond) for privileged accounts, such as IT admins and other roles with control of business-critical systems.
- Why: This slows or blocks attackers from gaining complete access to steal and encrypt your resources. Taking away the attacker’s ability to use IT admin accounts as a shortcut to resources will drastically lower the chances that they’ll be successful in controlling enough resources to impact your business and demand payment.
- How: Enable elevated security for privileged accounts—tightly protect, closely monitor, and rapidly respond to incidents related to these roles. See Microsoft’s recommended steps that:
- Cover end-to-end session security (including multifactor authentication for admins).
- Protect and monitor identity systems.
- Mitigate lateral traversal.
- Promote rapid threat response.
Step 3. Make it harder to get in: Incrementally remove risks
- What: Prevent a ransomware attacker from entering your environment, as well as rapidly respond to incidents and remove attacker access before they can steal and encrypt data.
- Why: This causes attackers to fail earlier and more often, undermining their profits. While prevention is the preferred outcome, it may not be possible to achieve 100 percent prevention and rapid response across a real-world organization with a complex multi-platform, multi-cloud estate and distributed IT responsibilities.
- How: Identify and execute quick wins that strengthen security controls to prevent entry and rapidly detect and evict attackers, while implementing a sustained program that helps you stay secure. Microsoft recommends following the principles outlined in the Zero Trust strategy. Against ransomware, organizations should prioritize:
- Improving security hygiene by reducing the attack surface and focusing on vulnerability management for assets in their estate.
- Implementing protection, detection, and response controls for digital assets, as well as providing visibility and alerting on attacker activity while responding to active threats.
The takeaway
To counter the threat of ransomware, it’s critical to identify, secure, and be ready to recover high-value assets—whether data or infrastructure—in the likely event of an attack. This requires a sustained effort involving obtaining buy-in from the top level of your organization (like the board) to get IT and security stakeholders working together asking nuanced questions. For example, what are the critical parts of the business that could be disrupted? Which digital assets map to these business segments (files, systems, databases)? How can we secure these assets? This process may be challenging, but it will help set up your organization to make impactful changes using the steps recommended above.
To learn more, visit our page on how to rapidly protect against ransomware and extortion.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
When you can’t trust your security vendor
We’ve been told “you must use an antivirus” for decades now, but what if it’s not really such great advice?
I use Norman. Not among the listed offenders and has stood me in very good stead for about 20 years.
http://www.itnews.com.au/blogentry/when-you-cant-trust-your-security-vendor-413732
Schneier on Security
An interesting read on digital security, including emails.
https://www.schneier.com/crypto-gram/archives/2015/1115.html
Email Oz Post Scam
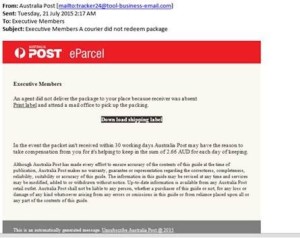
This is an urgent notification about a wave of Australia Post imitation emails designed to infect computers with a new Cryptolocker malware which maliciously encrypts local and network files.
Be vigilant, do not click on any links in emails for missed parcel notifications.
The following is an example of an imitation email that is being sent.
The emails are sent from the following or similar addresses:
track@tool-business-email.com
track24@tool-business-email.com
tracker@tool-business-email.com
tracker24@tool-business-email.com
tracking@tool-business-email.com
tracking24@tool-business-email.com
info24@tool-business-email.com
It is important to not click on the link in the email and delete the email immediately.
If you accidentally click on the link in the email, immediately close your browser and do not enter the displayed code which downloads the malicious attachment.

