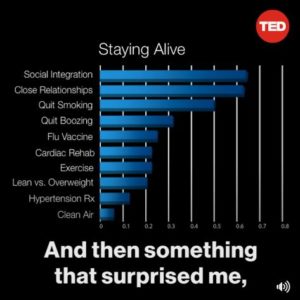
Number 5 contradicts other data I have so I call that questionable, but the rest is interesting!
Wireless Warfare Exposed – Declassified Military Doc Proves Smart Phones Are Killing Mankind

We’ve been treated like guinea pigs and the lab results are in…smart phones are killing us! Please watch this video.
https://www.youtube.com/watch?v=WLDdS4_Qneg
A Paper Run?
Sensational Voice

If you want to be moved to tears by an incredibly pure voice, watch and listen!
https://www.youtube.com/watch?v=pBPBFnVnPLg
On Marijuana
I see posts promoting the legalisation of marijuana, how the drug is harmless, it’s not a gateway drug etc., etc., etc.
Well, that contradicts the data I have. I mentioned this to a banjo treacher and he was vehement in his response to the contrary. So much so that he instantly agreed to pen his experience.
Now before you read Geoffrey’s words let me admit a bias, a prejudice, a vested interest if you will. Neither he nor I make a brass razoo, not a penny, not even diddle squat, wheher you do or don’t do drugs.
What I do get from you staying clean is the benefit of a happier, more aware, more intelligent you, more capable and with more of your attention in present time rather than stuck in the past. That has to be a big benefit to society and long-term, to my children and grand children.
Over to Geoffrey:
I am a musician. I grew up in the days of hippies and dope smoking in the 60s and 70s. Everyone, especially young people did all kinds of marijuana, hashish, canabis oil, any sort of pot, dope, bongs, smoking, sniffing… …ALL the stuff… …we were promised relaxation and the doors to a more creative world of kookie funkiness and lots of love and all things magical and mystical… …I grew my own, sold it and tried it all so I KNOW what I am talking about.
Marijuana is DEADLY… …and I don’t mean that in the cool Australian way… …it leads to a DEAD Head… …and we all have seen how stupid stoners look and act… …the promise of marijuana “relaxation“ is a FRAUD. I lived with the psychotic after effects and disoriented living that drugs like that produce… …they do nothing but DAMAGE. I am 63 years of age and I just spent a small fortune to handle the bad effects of this drug on my body but most of all on my MIND. It’s terrible what confusion and inability to think that long term drug use causes. After the drug detox I CAN think and I am NOT confused and it’s because I got RID of the restimulative effects of drugs from my body!
ANYONE who tells you this drug is OK is either ill informed, stupid or BOTH… …or has another agenda. Get OFF drugs and find out why you did them. Don’t listen to idiots go on about the positive points of pot. Marijuana is a MIND KILLER and physically dangerous.
Geoffrey White
I read from someone who had done a lot of work on drugs that every person who turns to medical or recreational drugs does so to escape pain, mental or physical.
I read elsewhere that the most money can be made from helping people avoid confronting their problems.
The trouble is that drugs do reduce the pain you feel. Unfortunately they reduce every emotion you feel.
I have a very nice guy I know who first got onto drugs (Ritalin) from a school counsellor, graduated to recreational drugs and has not stopped using them since. His biggest fear? The deadness he feels when not high.
This deadness, this detachment, this lack of feeling or empathy is why a kid can pick up a gun and kill a dozen or more of their classmates.
If you have any questions or are looking for suggestions, feel free to drop me a line.
Vitamin B12: 4 Health Benefits, 4 Symptoms Of Deficiency, And 4 Foods To Eat

OK my vegan friends, please be aware. Klamath Blue Green Algae is the only non-flesh source of B12 of which I know that is assimilable by the body. Most vegetable source of B12 are analogues, not absorbed by the body. That’s why I use Klamath ion my vegetarian powders and bars. I don’t want you missing out!
https://www.curejoy.com/content/vitamin-b12-essential-symptoms-foods/
Monsanto’s Roundup Weedkiller Destroys Life in Humans and Our Soils

If you are not make a conscious, deliberate and concerted effort to keep all GMOs and other Roundup tainted food out of your diet you are not doing the best for your future health you can do!
It’s that simple
https://www.organicconsumers.org/blog/monsantos-roundup-weedkiller-destroys-life-humans-and-our-soils
Corporate Monopolies Will Accelerate the Globalisation of Bad Food, Poor Health and Environmental Catastrophe
by Rosemary Mason – Colin Todhunter January 19, 2018
If the proposed Monsanto-Bayer merger goes through, the new company would control more than 25 per cent of the global supply of commercial seeds and pesticides. Monsanto held a 26% market share of all seeds sold in 2011. Bayer sells 17% of the world’s total agrochemicals and also has a seeds sector. If competition authorities pass the deal, the combined company would be the globe’s largest seller of both seeds and agrochemicals.
It marks a trend towards consolidation in the industry with Dow and DuPont having merged and Swiss seed/pesticide giant Syngenta merging with ChemChina. The mergers would mean that three companies would dominate the commercial agricultural seeds and chemicals sector.
In response to the Monsanto-Bayer merger, after it was announced in 2016 the US National Farmers Union President Roger Johnson issued the following statement:
“Consolidation of this magnitude cannot be the standard for agriculture, nor should we allow it to determine the landscape for our future… We will continue to express concern that these megadeals are being made to benefit the corporate boardrooms at the expense of family farmers, ranchers, consumers and rural economies… [there is an] alarming trend of consolidation in agriculture that has led to less competition, stifled innovation, higher prices and job loss in rural America.”
For all the rhetoric that we often hear about ‘the market’ and large corporations offering choice to farmers and consumers, the evidence is restriction of choice and the squeezing out of competitors. Over the years, for instance, Monsanto has bought up dozens of competitors to become the largest supplier of genetically engineered seeds with seed prices having risen dramatically.
Consolidation and monopoly in any sector should be of concern to everyone. But the fact that the large agribusiness conglomerates specialize in a globalised, industrial-scale, chemical-intensive model of farming should have us very concerned. Farmers are increasingly reliant on patented corporate seeds, whether non-GM hybrid seeds or GM and the chemical inputs designed to be used with them. Monsanto seed traits are now in 80% of corn and more than 90% of soybeans grown in the US.
By its very nature, the economic model that corporate agriculture is attached to demands expansion, market capture and profit growth. It might bring certain benefits to those farmers who have remained in agriculture, if not for the 330 farmers in the US who leave their land every week (according to data from the National Agricultural Statistics Service).
But in the US, ‘success’ in agriculture has largely depended on over $51 billion of taxpayer handouts over a 10-year period to oil the wheels of a particular system of agriculture designed to maintain corporate agribusiness profit margins. And any ‘success’ fails to factor in all the external social, health and environmental costs. It is easy to spin failure as success when the parameters are narrowly defined.
Moreover, the exporting of Green Revolution ideology and technology throughout the globe has been a boon to transnational seed and agrochemical manufacturers, which have benefited from undermining a healthy, sustainable indigenous agriculture.
The main players in the global agribusiness sector rank among the Fortune 500 corporations. These companies are high-rollers in a geo-politicised, globalised system of food production whereby huge company profits are linked to the worldwide eradication of the small farm (the bedrock of global food production), bad food, poor health, rigged trade, environmental devastation, mono-cropping and diminished food and diet diversity, the destruction of rural communities, ecocide, degraded soil, water scarcity and drought, destructive and inappropriate models of development and farmers who live a knife-edge existence and for whom debt has become a fact of life.
Does the world need it?
Britain is a leader in intensive, corporate-dominated agriculture. But is this the model of agriculture the world should rely on?
Let us turn to campaigner and environmentalist Dr Rosemary Mason to appreciate some of the consequences of this model. She has just written an open letter to Professor Dame Sally Davies, Chief Medical Officer for England and Chief Medical Advisor to the UK government. Although written to Davies, the letter is intended for the four Chief Medical Officers of Health for England, Scotland, Wales and Ireland and Public Health England.
Her letter is essentially a plea to highly placed officials to act.
Mason provides a stark reminder of the impacts of the agrochemical/agribusiness sector, its political power and its effects on health. She draws attention to a report by the UN Special Rapporteur on the right to food, which states unequivocally that the storyline perpetuated by the likes of Bayer’s Richard van der Merwe (in this piece) saying we need pesticides and (often chemical-dependent) GMOs to feed the world is a myth.
The report is severely critical of the global corporations that manufacture pesticides, accusing them of the “systematic denial of harms”, “aggressive, unethical marketing tactics” and heavy lobbying of governments which has “obstructed reforms and paralysed global pesticide restrictions”.
The authors of the report call for a comprehensive new global treaty to regulate and phase out the use of dangerous pesticides in farming and move towards sustainable agricultural practices. They say:
“excessive use of pesticides is very dangerous to human health, to the environment and it is misleading to claim they are vital to ensuring food security.”
Mason notes that chronic exposure to pesticides has been linked to cancer, Alzheimer’s and Parkinson’s diseases, hormone disruption, developmental disorders and sterility. Certain pesticides can persist in the environment for decades and pose a threat to the entire ecological system on which food production depends.
One of the report’s authors, the UN expert on Toxics Baskut Tuncak, wrote in the Guardian:
“Our children are growing up exposed to a toxic cocktail of weedkillers, insecticides, and fungicides. It’s on their food and in their water, and it’s even doused over their parks and playgrounds. The UN Convention on the Rights of the Child, the most ratified international human rights treaty in the world (only the US is not a party), makes it clear that states have an explicit obligation to protect children from exposure to toxic chemicals, from contaminated food and polluted water, and to ensure that every child can realise their right to the highest attainable standard of health. These and many other rights of the child are abused by the current pesticide regime. These chemicals are everywhere and they are invisible. The only way to protect citizens, especially those disproportionately at risk from exposure, is for governments to regulate them effectively, in large part by adhering to the highest standards of scientific integrity.
Mason offers Sally Davies and her colleagues evidence that suggests rising UK Mortality rates point to a critical, unprecedented health epidemic. Arguing that the heavy use of agrochemicals in the UK is a major contributory factor, she notes Cancer Research UK (CRUK) is protecting the agrochemical industry due to its strategic influence. As a result, the mainstream narrative on cancer focuses on the role of alcohol (see this also) and ‘lifestyle choices’ while sidelining the strong evidence that agrochemicals are having.
Rosemary Mason asks Sally Davies if she is aware that the UK Department of Health is working with industry, again citing evidence in support of her claim.
As someone who has written extensively on the adverse impacts of glyphosate, Mason refers Davies to research that links Monsanto’s glyphosate-based Roundup with liver damage.
If the National Health Service in the UK is experiencing a crisis – as indeed it is – due to rising rates of morbidity (not withstanding the effects of poor funding and creeping privatisation), surely these spiralling rates of diseases must be addressed. And where better to start by shining the light on agrochemicals rather than blaming individuals for lifestyle choices and alcohol consumption?
For instance, a report by ‘Children with Cancer UK’ in 2016 said there were 1,300 more cases per year of cancers in children, particularly in young adults, compared with 1998. While the medical correspondent from The Telegraph has mentioned pesticides as a possible cause, a spokesperson from CRUK said there is no evidence of environmental factors.
Among the various statistics Mason provides are those indicating that colon cancer had risen by 200%, thyroid cancer has doubled, ovarian cancer is up by 70% and cervical cancer is up by 50% since 1998.
Yes, despite the evidence, the corporate media in Britain is silent about pesticides, which partly results from the corporate sponsorship of the UK Science Media Centre; so any science against the corporations can be suppressed by interested parties, including AstraZeneca, Coca Cola, Syngenta, BP and Monsanto.
While Mason produces figures to show the massive increase in a range of agrochemicals over the years, the Chief Scientist for the Department of Environment, Food and Rural Affairs, Professor Ian Boyd, points out that once a pesticide is approved there is no follow up. There is also no follow up as to the impacts of not just one chemical but the cocktail of agrochemicals out there and how they interact when in the human body and within the environment.
And let’s not forget that many of these agrochemicals were fraudulently placed on the commercial market in the first place without proper testing.
Readers can read Mason’s letter in full here, where she also discusses a potential UK-US trade deal with the US and the impacts on the lowering of food and environmental standards and subsequent relations with the EU.
The impacts of the Monsanto-Bayer deal and the contents of Rosemary’s letter to the Chief Medical officers of the UK are just the tip of an iceberg. There is a lot more that could and has been said on the impact of agribusiness giants on the globalisation of bad food and poor health, ecological degradation, soil health, ocean dead zones as well as the chemical contamination of our food by the handful of food conglomerates that now increasingly dominate the supply chain.
Alternative approaches and solutions exist but the political influence and financial clout of transnational corporations means that ‘business as usual’ prevails.
https://www.counterpunch.org/2018/01/19/corporate-monopolies-will-accelerate-the-globalisation-of-bad-food-poor-health-and-environmental-catastrophe/
Spectre and Meltdown Attacks Against Microprocessors
The security of pretty much every computer on the planet has just gotten a lot worse, and the only real solution — which of course is not a solution — is to throw them all away and buy new ones.
On January 3, researchers announced a series of major security vulnerabilities in the microprocessors at the heart of the world’s computers for the past 15-20 years. They’ve been named Spectre and Meltdown, and they have to do with manipulating different ways processors optimize performance by rearranging the order of instructions or performing different instructions in parallel. An attacker who controls one process on a system can use the vulnerabilities to steal secrets elsewhere on the computer.
This means that a malicious app on your phone could steal data from your other apps. Or a malicious program on your computer — maybe one running in a browser window from that sketchy site you’re visiting, or as a result of a phishing attack — can steal data elsewhere on your machine. Cloud services, which often share machines amongst several customers, are especially vulnerable. This affects corporate applications running on cloud infrastructure, and end-user cloud applications like Google Drive. Someone can run a process in the cloud and steal data from every other user on the same hardware.
I am sure people thought me weird and old fashioned because I would not subscribe to the Cloud philosophy. This is exactly one reason why. – Tom)
Information about these flaws has been secretly circulating amongst the major IT companies for months as they researched the ramifications and coordinated updates. The details were supposed to be released next week, but the story broke early and everyone is scrambling. By now all the major cloud vendors have patched their systems against the vulnerabilities that can be patched against.
https://www.schneier.com/crypto-gram/archives/2018/0115.html


